Use Application Load Balancers for blue-green and canary deployments
Blue-green deployments and rolling deployments (canary tests) let you release new software gradually, reducing the potential blast radius of a failed software release. This workflow lets you publish software updates with near-zero downtime.
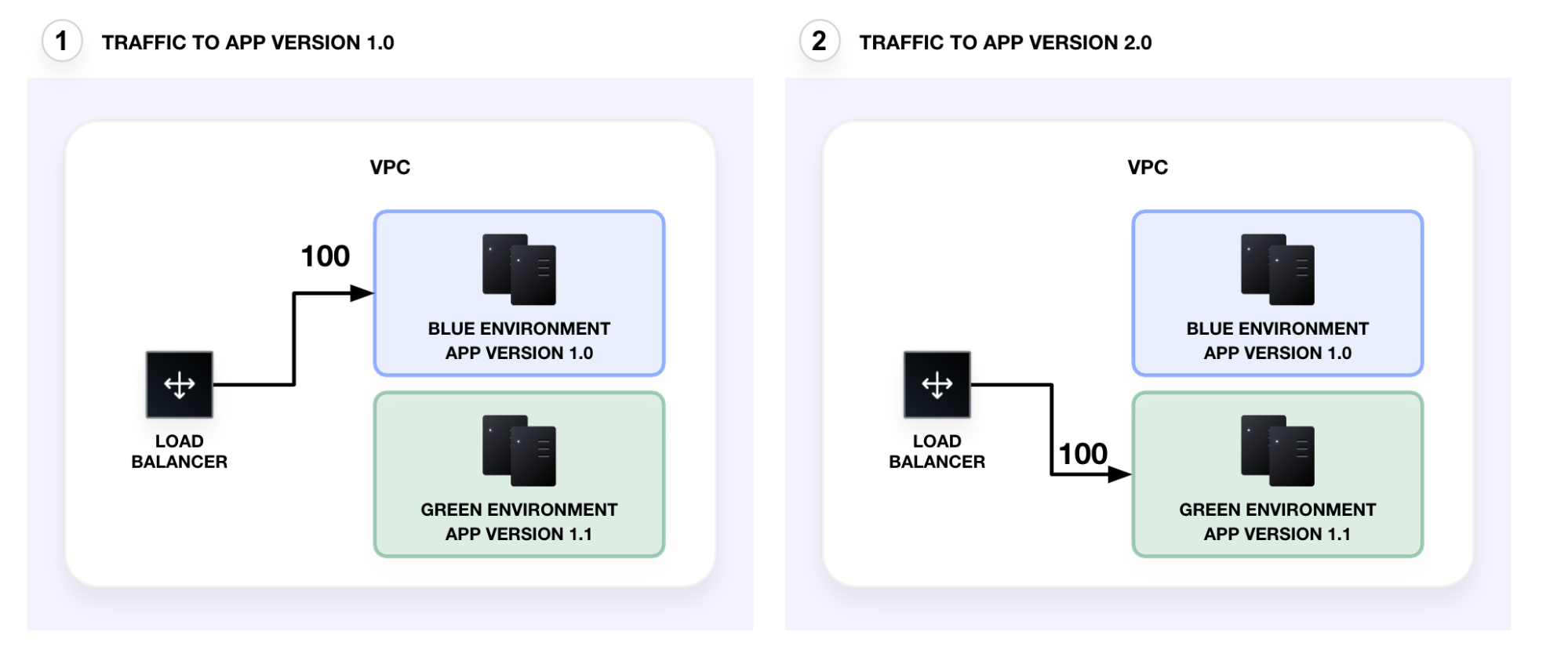
In a blue-green deployment, the current service deployment acts as the blue environment. When you are ready to release an update, you deploy the new service version and underlying infrastructure into a new green environment. After verifying the green deployment, you redirect traffic from the blue environment to the green one.
This workflow lets you:
- Test the green environment and identify any errors before promoting it. Your configuration still routes traffic to the blue environment while you test, ensuring near-zero downtime.
- Easily roll back to the previous deployment in the event of errors by redirecting all traffic back to the blue environment.
Canary tests and rolling deployments release the new version of the service to a small group of users, reducing the blast radius in the event of failure.
You can use blue-green deployments for canary tests. After the green environment is ready, the load balancer sends a small fraction of the traffic to the green environment (in this example, 10%).
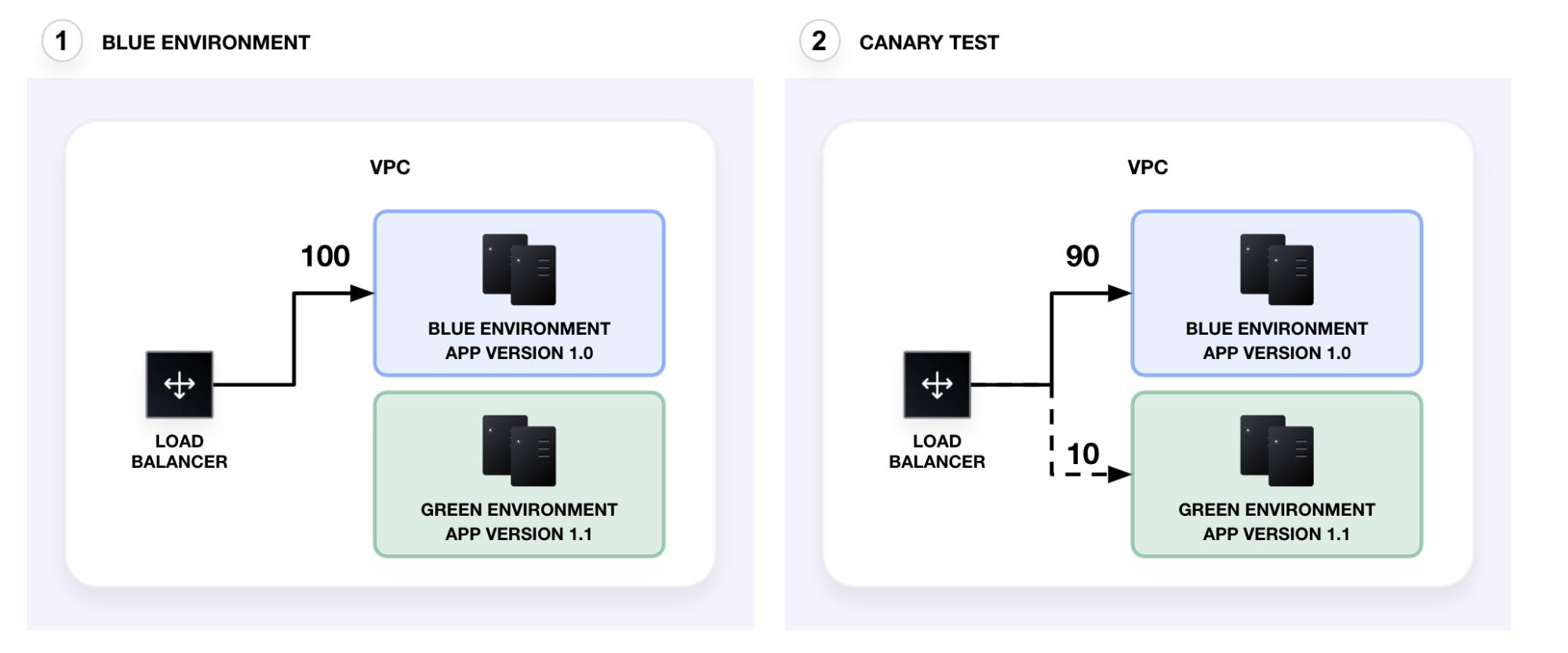
If the canary test succeeds without errors, you incrementally direct traffic to the green environment (50/50 — split traffic). Finally, you redirect all traffic to the green environment. After verifying the new deployment, you can destroy the old, blue environment. The green environment is now the current production service.
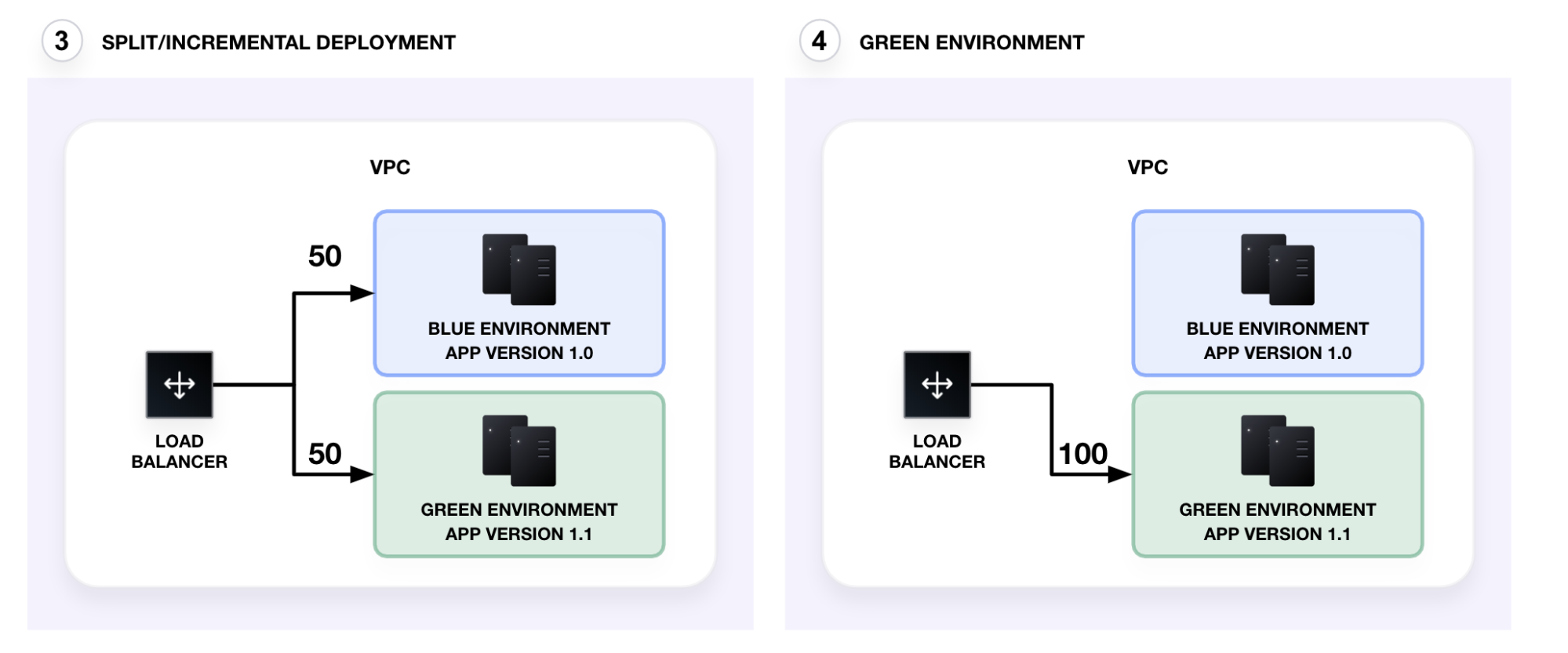
AWS's application load balancer (ALB) lets you define rules that route traffic at the application layer. This differs from classic load balancers, which only let you balance traffic across multiple EC2 instances. You can define an ALB's listeners (rules) and target groups to dynamically route traffic to multiple services. These rules let you run canary tests on and incrementally promote the green environment.
In this tutorial, you will use Terraform to:
- Provision networking resources (VPC, security groups, load balancers) and a set of web servers to serve as the blue environment.
- Provision a second set of web servers to serve as the green environment.
- Add feature toggles to your Terraform configuration to define a list of potential deployment strategies.
- Use feature toggles to conduct a canary test and incrementally promote your green environment.
Prerequisites
This tutorial assumes you are familiar with the standard Terraform workflow. If you are unfamiliar with Terraform, complete the Get Started tutorials first.
For this tutorial, you will need:
- Terraform 1.3+ installed locally
- an AWS account
Review example configuration
Clone the Learn Terraform Advanced Deployment Strategies repository.
Navigate to the repository directory in your terminal.
This repository contains multiple Terraform configuration files:
main.tfdefines the VPC, security groups, and load balancers.variables.tfdefines variables used by the configuration such as region, CIDR blocks, number of subnets, etc.blue.tfdefines 2 AWS instances that run a user data script to start a web server. These instances represent "version 1.0" of the example service.init-script.shcontains the script to start the web server.terraform.tfdefines theterraformblock, which specifies the Terraform binary and AWS provider versions..terraform.lock.hclis the Terraform dependency lock file.
Note
This example combines the network (load balancer) and the application configuration in one directory for convenience. In a production environment, you should manage these resources separately to reduce the potential blast radius of any changes.
Review main.tf
Open main.tf. This file uses the AWS provider to deploy the base infrastructure for this tutorial, including a VPC, subnets, an application security group, and a load balancer security group.
The configuration defines anaws_lb resource which represents an ALB. When the load balancer receives the request, it evaluates the listener rules, defined by aws_lb_listener.app, and routes traffic to the appropriate target group.
This load balancer currently directs all traffic to the blue load balancing target group on port 80.
Review blue.tf
Open blue.tf. This configuration defines two AWS instances that start web servers, which return the text Version 1.0 - #${count.index}. This represents the sample application's first version and indicates which server responded to the request.
This file also defines the blue load balancer target group and attaches the blue instances to it using aws_lb_target_group_attachment.
Initialize and apply the configuration
In your terminal, initialize your Terraform configuration.
Apply your configuration. Respond yes to the prompt to confirm the operation.
Verify blue environment
Verify your blue environment by visiting the load balancer's DNS name in your browser or cURLing it from your terminal.
Note
It may take a few minutes for the load balancer's health checks to pass and the web servers to respond.
Notice that the load balancer evenly distributes traffic between the two instances in the blue environment.
Deploy green environment
Create a new file named green.tf and paste in the configuration for the sample application's version 1.1.
Notice how this configuration is similar to the blue application, except that the web servers return green #${count.index}.
Add the following variables to variables.tf.
Apply your configuration to deploy your green application. Remember to confirm your apply with a yes.
Add feature toggles to route traffic
Even though you deployed your green environment, the load balancer does not yet route traffic to it.
While you could manually modify the load balancer's target groups to include the green environment, using feature toggles codifies this change for you. In this step, you will add a traffic_distribution variable and traffic_dist_map local variable to your configuration. The configuration will update the target group's weight based on the traffic_distribution variable.
First, add the configuration for the local value and traffic distribution variable to variables.tf.
Notice that the local variable defines five traffic distributions. Each traffic distribution specifies the weight for the respective target group:
- The
bluetarget distribution is the current distribution — the load balancer routes 100% of the traffic to the blue environment, 0% to the green environment. - The
blue-90target distribution simulates canary testing. This canary test routes 90% of the traffic to the blue environment and 10% to the green environment. - The
splittarget distribution builds on top of canary testing by increasing traffic to the green environment. This splits the traffic evenly between the blue and green environments (50/50). - The
green-90target distribution increases traffic to the green environment, sending 90% of the traffic to the green environment, 10% to the blue environment. - The
greentarget distribution fully promotes the green environment — the load balancer routes 100% of the traffic to the green environment.
Modify the aws_lb_listener.app's default_action block in main.tf to match the following. The configuration uses lookup to set the target groups' weight. Notice that the configuration defaults to directing all traffic to the blue environment if no value is set.
Note
The ELB's stickiness is set to false and 1 second to demonstrate traffic routing between the two target groups. Refer to AWS's guidance on these settings for production environments.
Begin canary test
Apply your configuration with the traffic_distribution variable set to blue-90 to run a canary test. Remember to confirm your apply with a yes.
Verify canary deployment traffic
Verify that your load balancer now routes 10% of the traffic to the green environment.
Note
It may take a few minutes for the load balancer's health checks to pass and for the green environment to begin responding.
Notice that the load balancer now routes 10% of the traffic to the green environment.
Increase traffic to green environment
Now that the canary deployment was successful, increase the traffic to the green environment.
Apply your configuration with the traffic_distribution variable set to split to increase traffic to the green environment. Remember to confirm your apply with a yes.
Verify rolling deployment traffic
Verify that your load balancer now splits the traffic to the blue and green environments.
Note
It may take a few minutes for the load balancer's health checks to pass. The results may not always show an exact 50/50 distribution when running the following command.
Notice that the load balancer now evenly splits the traffic between the blue and green environments.
Promote green environment
Since both the canary and rolling deployments succeeded, route 100% of the load balancer's traffic to the green environment to promote it.
Apply your configuration to promote the green environment by setting the traffic_distribution variable to green. Remember to confirm your apply with a yes.
Verify load balancer traffic
Verify that your load balancer now routes all traffic to the green environment.
Note
It may take a few minutes for the load balancer's health checks to pass.
Using this deployment strategy, you successfully promoted your green environment with near-zero downtime.
Scale down blue environment
After verifying that your load balancer directs all traffic to your green environment, it is safe to disable the blue environment.
Apply your configuration to destroy the blue environment resources by setting the traffic_distribution variable to green and enable_blue_env to false. Remember to confirm your apply with a yes.
Deploy new version
In this tutorial, you deployed the application's Version 1.0 in the blue environment, and the new version, 1.1, in the green environment. When you promoted the green environment, it became the current production environment. Deploy the next release to the blue environment, which minimizes modifications to your existing configuration by alternating the blue and green environments.

Modify the aws_instance.blue's user_data and tags blocks in blue.tf to display a new version number, 1.2.
Enable new version environment
Apply your configuration to provision the new version of your infrastructure. Remember to confirm your apply with a yes. Set the traffic_distribution variable to green to continue directly all traffic to your current production deployment in the green environment.
Start shifting traffic to blue environment
Apply your configuration to run a canary test to the blue environment by setting the traffic_distribution variable to green-90. Remember to confirm your apply with a yes.
Once the apply completes, verify that your load balancer routes traffic to both environments.
Note
It may take a few minutes for the load balancer's health checks to pass.
Promote blue environment
Now that the canary deployment is successful, fully promote your blue environment.
Apply your configuration to promote the blue environment by setting the traffic_distribution variable to blue. Remember to confirm your apply with a yes.
Verify that your load balancer now routes all traffic to the blue environment.
Note
It may take a few minutes for the load balancer's health checks to pass.
You now used blue-green, canary, and rolling deployments to safely deploy two releases.
Clean up your infrastructure
Destroy the resources you provisioned. Remember to respond to the confirmation prompt with yes.
Next steps
In this tutorial, you used Terraform to incrementally deploy a new application release. You implemented feature toggles to perform blue-green deployments and canary testing, helping you consistently and reliably use these advanced deployment techniques.
To learn how to automate your infrastructure deployment process and schedule near-zero downtime releases, review the following resources.